Last update at :2024-01-02,Edit by888u
Vpsadd tutorial: Linux firewalliptables security issues Settings such as prohibiting PING and outbound packets
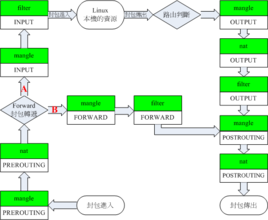
iptables -t filter: As the name suggests, when used for filtering nat: As the name suggests, it is used when doing NAT -A, -I, -D, -R, -P, -F APPEND, add a rule INSERT, insert a rule DELETE, delete a rule REPLACE, replace a rule POLICY, set the default rules for a certain chain FLUSH, clear rules INPUT: Located in the filter table, matching packets whose destination IP is the local machine FORWARD: Located in the filter table, matching data packets passing through the machine, PREROUTING: Located in the nat table, used to modify the destination address (DNAT) POSTROUTING: Located in the nat table, used to modify the source address (SNAT) -i, -o Incoming and outgoing interfaces -i ppp0 -s, -d Source, destination address -s192.168.0.1 matches packets from 192.168.0.1 -s 192.168.1.0/24 matches packets from the 192.168.1.0/24 network -p agreement type -p icmp –icmp-type type -p tcp –sport, –dport Source, destination port –sport1000 matches packets with source port 1000 –sport 1000:3000 matches packets with source ports 1000-3000 (including 1000 and 3000) –sport:3000 matches packets whose source port is below 3000 (inclusive) –sport1000: Match packets whose source port is above 1000 (inclusive) -m state –state NEW, RELATED, ESTABLISHED, INVALID mac –mac-source xxxxxxx limit –limit 50/s -m multiport –dports 21,22,25,80,110 -j ACCEPT DROP SNAT DNAT MASQUERADE
Typical applications: iptables -t nat -A PREROUTING -i ppp0 -p tcp –dport 80 \ -j DNAT –to192.168.1.1 Do dnat and provide web services on the intranet iptables -t nat -A POSTROUTING -s 192.168.0.0/24 \ -j SNAT –to1.1.1.1 Do snat and provide Internet access services for the intranet
-L [chain name] LIST, list the rules v: Display detailed information, including the number of matching packets and the number of matching bytes for each rule x: Based on v, automatic unit conversion is prohibited (K, M) n: Only the IP address and port number are displayed, but the domain name and service name are not displayed
All chain names must be in uppercase letters
INPUT/OUTPUT/FORWARD/PREROUTING/POSTROUTING
All table names must be lowercase
filter/nat/mangle
All actions must be capitalized
ACCEPT/DROP/SNAT/DNAT/MASQUERADE
All matches must be lowercase
-s/-d/-m
1. Use iptables rules to ban ping
iptables -A INPUT -p icmp –icmp-type 8 -s 0/0 -j DROP 2. Use iptables rules to prohibit the server from sending packets to the outside and prevent DDOS attacks from outside
iptables -I OUTPUT -p udp –dport 53 -d 8.8.8.8 -j ACCEPT #Allow UDP service IP iptables -A OUTPUT -p udp -j DROP #Disable udp service The above ports 53 and 8888 are required for DNS service. If you don’t know the DNS settings of this machine, you can execute the following command to get the IP:
cat /etc/resolv.conf
DoS attack prevention
Using the extension module limit, we can also configure iptables rules to prevent DoS attacks:
iptables -A INPUT -p -tcp –dport 80 -m limit –limit 25/minute –limit-burst 100 -j ACCEPT –litmit 25/minute indicates that the maximum number of connections per minute is limited to 25
–litmit-burst 100 indicates that when the total number of connections exceeds 100, start the litmit/minute limit
Use iptables rules to prohibit the server from sending packets to the outside to prevent DDOS attacks. If the service uses SMTP to send emails similar to WordPress, it is best not to use these two commands, otherwise the email will not be sent.
Recommended site searches: ip online agent Hong Kong domain name registration, German server, ASP host space, website icp filing, filing system, virtual host evaluation, Hong Kong server purchase, free mainland China space, American website server,







发表评论